1. Are you covered? – 2. The process – 3. 3. Price calculator
Achieving NIS 2 compliance is a comprehensive process where individual starting points converge towards the same goal. It simply means that you are going on a journey of maturity that can take up to several years, depending on your starting point. The path towards the goal is generally the same for everyone, but the size of the challenges that arise along the way can vary considerably.
Based on our many years of expertise and experience in cyber and information security have Unitas organized a transparent and pragmatic process that is based on the ISO27001/2 standard.
If you want the full and detailed overview with stakeholders and output from the individual phases, you can click here. The overview will be sent automatically within a few minutes.
Implementation
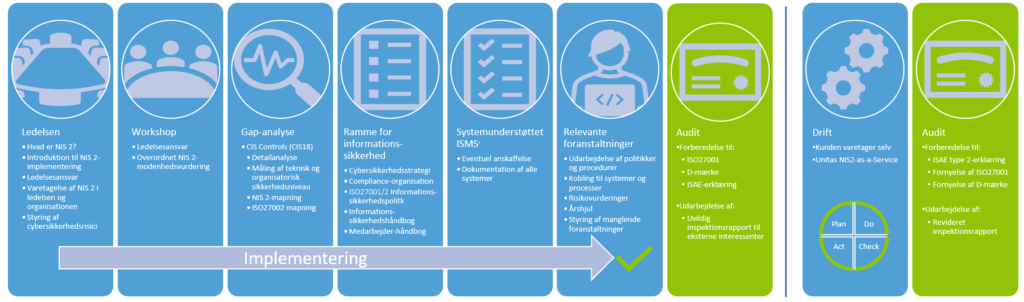
The management plays a large and central role in a successful implementation and subsequent operation of NIS 2. It is therefore essential that the management knows thoroughly about NIS 2, gets a deep insight into roles, responsibilities and the ongoing work in the organization – even after NIS 2 is implemented.
Unitas offers a focused management introduction to NIS 2 for the executive board, board of directors and other relevant top management. You must put approx. 3 hours to it. This is where it all starts!
The next step in the process continues with a workshop, where we together identify the challenges and barriers that must be overcome on the way to compliance with NIS 2. We establish a common understanding of management's responsibilities in relation to NIS 2 and prepare a management report that contains an overall plan for the rest of the process.
We thenperform a Gap analysis. We use the CIS Controls framework. CIS Controls measures your maturity against 18 technical measures, all of which aim – like NIS 2 – to reduce your cyber and information security risk. Since many of the 18 measures overlap with the requirements that NIS 2 places on you, you will be able to get a good indication of where you are right now and the milestones that must be met along the way. However, we naturally start from what you may already have in advance of relevant documentation, just as any recently carried out CIS Controls measurement or equivalent, will be able to be reused to a greater or lesser extent.
A central part of the implementation of NIS 2 consists in is that create the framework for cyber and information security efforts. Based on an overall cyber security strategy that is anchored in top management, we translate the strategy into an information security policy based on ISO27001, which is in turn anchored by management. On this basis, an overview of the measures from ISO27002 that already exist and which must either be improved or established in the organization for the first time in order to meet NIS 2 is prepared.
The improvement and/or establishment of the measures is done on the basis of risk assessments and more practically by preparing subject-specific policies. These policies must be seen as the management's order to the rest of the organization to follow the policies to ensure precisely the level of cyber and information security that the management has set in the cyber security strategy and the information security policy, and which the risk assessments have shown to be necessary. However, the policies can also be called standards, guidelines, directives or handbooks, as we have called them below, according to your way of communicating.
The policies may cover, for example, access management, physical and environmental security, asset management, network security and backup and must typically be complied with by the IT department in particular, both internally and in relation to IT suppliers, some of whom will also be your data processors.
We then describe the requirements more simply and comprehensibly in an easy-to-read employee-oriented manner manual, which deal with specific areas related to the individual work functions in the organisation. Depending on the circumstances, more can be prepared further targeted handbooks for example Purchasing, HR and Facility.
The documentation is crucial for compliance! When the above is in place, you have established a so-called management system for information security (ISMS). It is the formally correct name in an ISO27001 context. ISMS means – cut to the bone – that the management takes responsibility for and manages your cyber and information security efforts, which the management must precisely do according to NIS 2.
Operation of ISMS in an annual cycle: As the ISMS must be revised and improved on the basis of the ongoing risk assessments and perhaps certified, there is no point in the ISMS lying around in Word and Excel files. It must be collected in one ISMS supporting IT system (GRC system) – that is, in an IT solution. If you already have an IT solution, we naturally start from that.
If you have not already chosen an IT solution, we will help you identify your need for IT support. We thus have tools such as Wired Relations og cyber day available that can carry out the task. In addition to NIS 2, most GRC systems can simultaneously solve the task of documenting compliance with other sets of rules, including, but not limited to, GDPR, PCI DSS, customers' special needs, sector legislation, etc.
Operation and improvement
When the documentation is in place in the IT solution, the organization must comply with policies, handbooks, risk assessments on an ongoing basis, etc. Quite often compliance will mean that you must change your normal activities and work routines. At this stage, there may be a need for a culture change so that the ISMS does not simply end up in the drawer, and you become vulnerable to cyber attacks and possible supervisory reactions, including fines for the organization and the management members.
Examples: It appears from the updated procurement policy that Procurement must ensure that cyber and information security is included as an element in all IT contracts, and that it must be checked that the IT suppliers actually comply with the security requirements. If, due to a lack of resources, Procurement is not already working with a cyber and information security track today, it is clear that the updated procurement policy means that Procurement will have to adjust some of its processes.
It may also be that your passwords need to be improved in light of your new password policy. Again, it may be that a behavior needs to be adjusted.
The alignment of your daily activities across the organization is called operating phase. In the operational phase, as mentioned, the measures selected in policies, handbooks, etc. are implemented. The aim is to improve the implementation of the measures based on risk assessments. Action is therefore naturally taken on any non-implemented measures or new risks that have been identified, which must be dealt with by assessing what is hindering implementation and possibly by revising the policy that describes what needs to be done. Finally, it is ensured that the policies have been properly communicated to the right people in the organisation.
We can take care of the operational phase for you, so that you get rid of the cost of a GRC function, and you are sure, among other things, that the organization contributes to NIS 2 compliance, and that the management regularly receives the statutory reporting on your cyber and information security efforts. See more below.
You are on target!
After a successful period of operation are you able to document compliance with the NIS 2 requirements, as well as adjust how you comply with NIS 2 when the Danish NIS 2 legislation is in place.
If desired, compliance can be sought to be demonstrated by staying The D brand. However, the D mark is not a guarantee that the authorities also believe that you fully comply with NIS 2, but merely an indication of this. If the ambition is greater than that, or you want to be ISO27001 certified, we will then organize the documentation so that an ISO27001 certification is possible.
So what now – who and how will our NIS 2 be operated going forward?
After implementation comes operation as usual. Here you can Unitas either equip internal employees to take care of the year's wheel's operational tasks, including management reporting, or you can choose to enter into a compliance-as-a-service agreement with Unitas, where we continuously handle the vast majority of NIS 2 tasks. This saves on expensive hiring, which has historically been difficult to retain.
You are now ready to try our NIS 2 price calculator.
1. Are you covered? – 2. The process – 3. 3. Price calculator
DO YOU WANT TO KNOW MORE ABOUT THE PROCESS?
Feel a little special and sign up Unitas' newsletter. Get very special offers and news that are not widely available on social media.
Feel a little special and sign up Unitas' newsletter. Get very special offers and news that are not widely available on social media.
