As a company, you must comply with existing and future laws, guidelines and other requirements for IT security. You must thus, among other things, be prepared for cyber attacks. You may have already been hit by successful attacks, so you know what that means. The insurance often also requires secure IT. All in all, you can say that the pressure comes from many sides, but it basically points to the same place: How should you as an IT manager in a large or small company find out what secure IT is for a size? And what is good enough so that we comply with the rules and so that we take care of our data? Questions that i.a. intrudes are, for example:
- How safe are we?
- Have we now got all areas covered?
- We have a limited budget: How do we get the most security for our money?
- How do we prioritize our efforts?
And then there is the company's management, which can be held accountable if things are not in order, and which therefore also pushes for answers to the real risk they face: Does the defense work if and when the attack comes? Can we keep them from penetrating the walls?
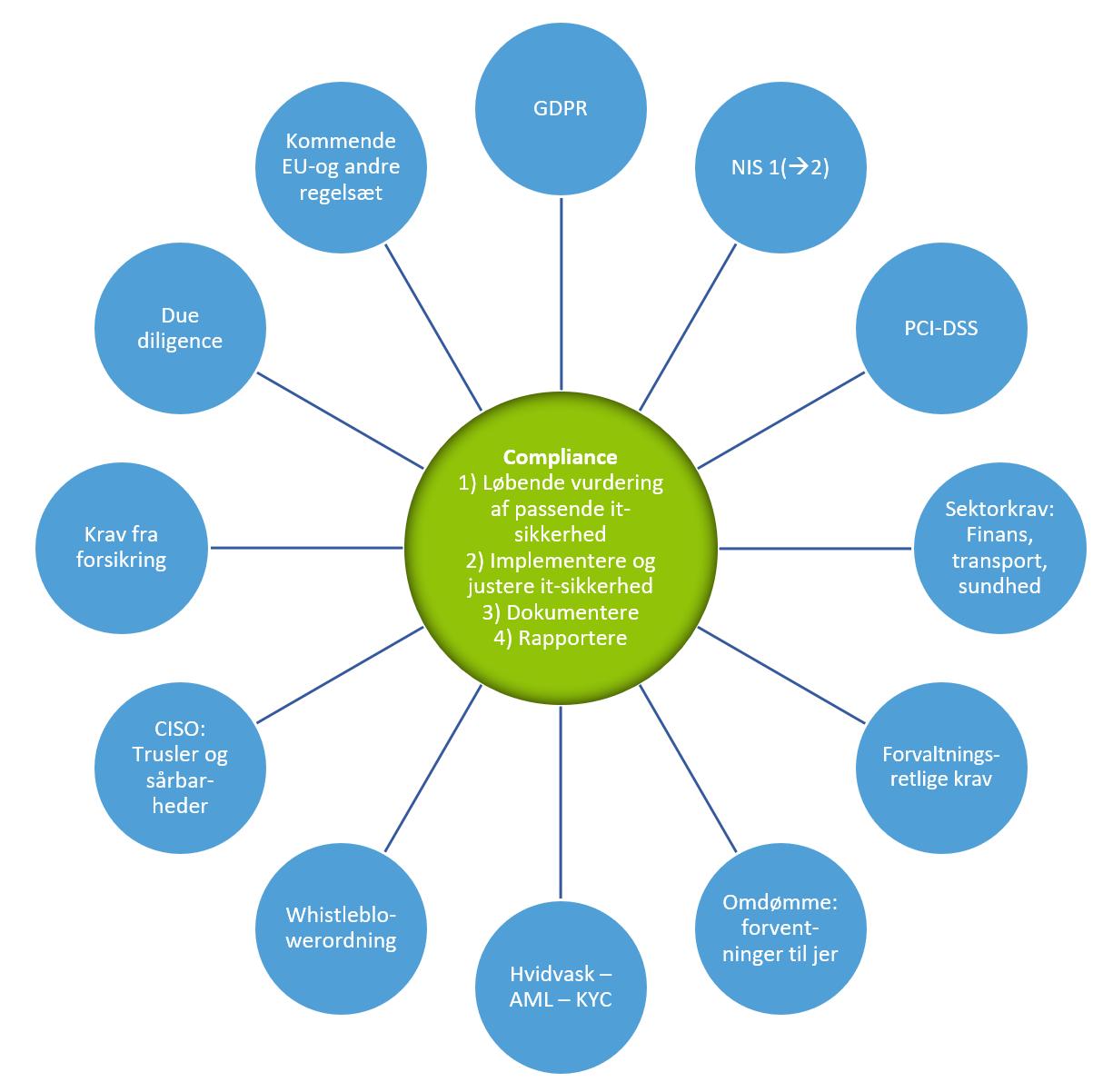
Should your company live up to specific sets of rules, eg GDPR or other legislation, there are 4 things that you need to be able to do;
- Ongoing assessment of implemented security
- Implement and adjust IT security
- Document
- Report
With a CIS Controls analysis, you get pkt. 1, 3 and 4, and thus you have already come a long way. You have an overview of the state of affairs, you get the overall management reports automatically generated and can therefore provide qualified answers on how the company's IT security is in relation to other comparable companies. Your IT auditor will also clap his hands, and you will proactively anticipate the IT auditor's questions.
Pkt. 2, which deals with the implementation and adjustment of IT security, on the other hand, requires specialist knowledge. Thus, the output of the analysis must be interpreted before you sit down with the roadmap that helps you, based on the current risks, to prioritize available finances and resources and give you a schedule. Maybe you yourself possess the competence for this, otherwise you can Unitas help you.
Unitas wants all companies to stand as strong as possible in the fight against cyber attacks. Whether you want our assistance or not, we can only recommend that you start with the CIS Controls analysis, and in this way you will expose the company's vulnerabilities and have a plan in place to strengthen the defense.
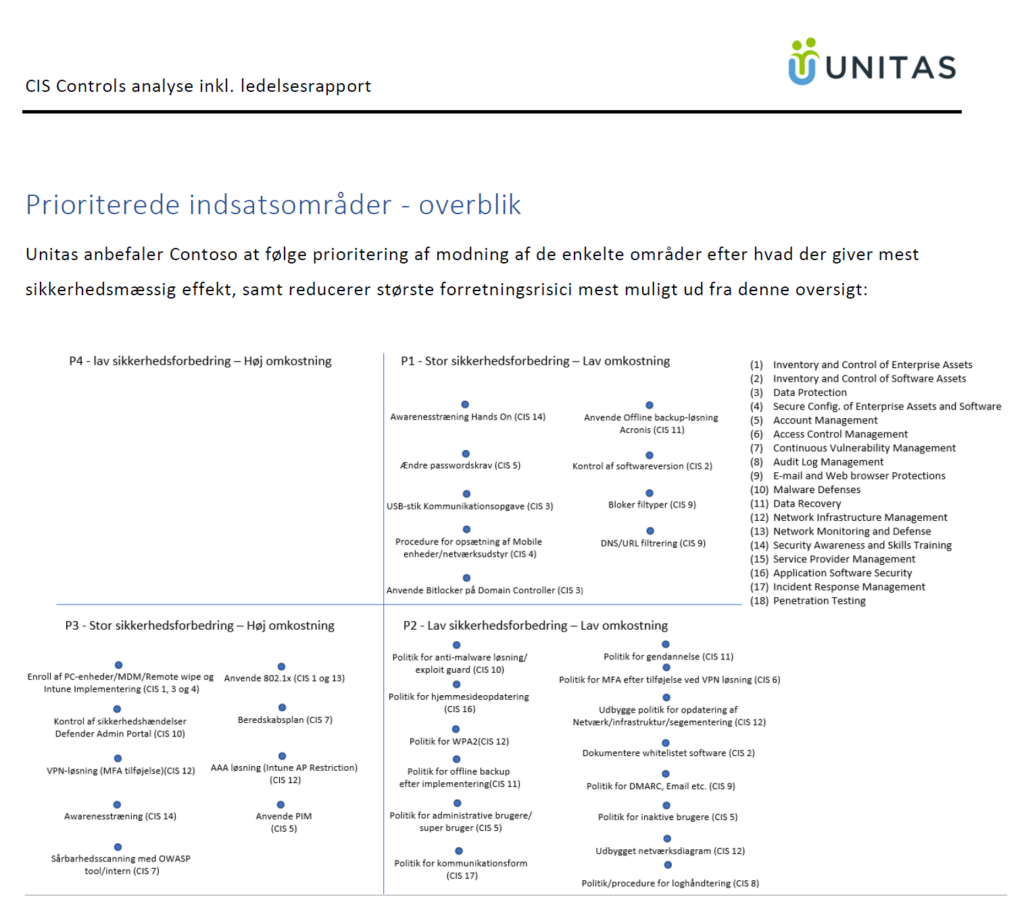
The end result of the analysis is i.a. this priority list of tasks. It therefore becomes very clear where the low-hanging fruits are based on the principle of maximum security for the least money or resources.
If you want a copy of an anonymized report, you can click here. Do not change anything in the subject field - just click 'Submit' and the report will be returned to you automatically. We use your e-mail address for nothing, so you do not have to fear being run out of doors.
You can read more about Unitas'CIS Controls analysis here .
A little about CISecurity
CISecurity is a completely independent organization that aims to help secure companies against cyber attacks by providing a range of tools. One among many is CIS Controls.
As a one-off show, the tool is free to use for a wide range of organizations and companies. If you find the tool valuable, you can buy a license or use a partner as Unitas, which has a service license, and you do not have to obtain a license yourself.
