Summary
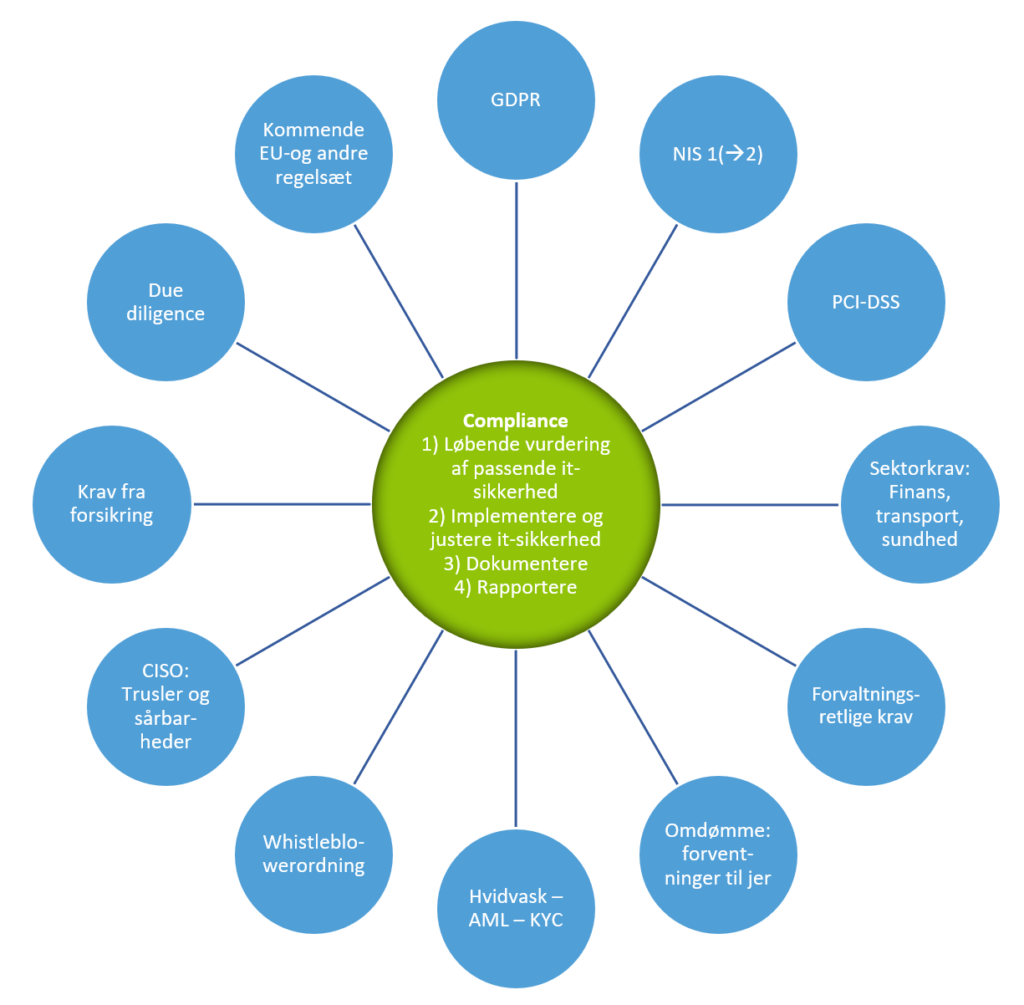
When you need to establish information and cyber security, you must start by assessing how much security you need and how expensive it will be to achieve in relation to your maturity. For work, you can be inspired by a well-known standard (ISO270XX, NIST SP 800-XXX, CIS18 or similar). First and foremost, you need to adapt your information and cyber security to the legal compliance requirements to which you are subject. The requirements are similar across general sets of rules (NIS2, GDPR, the Whistleblower Act, etc.) and sectoral laws (finance, health, transport, etc.).
Therefore, in other words, do not start with the law. Start with common sense. And stop linking your information and cyber security function to the rules you are subject to. So you avoid having to change every time new rules come or existing ones change.
We need to get out of the treadmill
NIS2 is on the doorstep, and we consultants have already started selling advice based on fears of fines and fears of cybercrime.
In addition to NIS2, at least the following are on the way, which in one way or another affect how we should process data: data governance act, artificial intelligence regulation, digital operational resilience for the financial sector, the EU cybersecurity act, data act, digital services act, critical entities resiliance directive, etc. Something is not adopted and something is adopted through other channels.
In addition, there is a tightening of the case law of known sets of rules such as the GDPR. We have thus seen over the years an increasing clarification of what is required. And it does not get easier with time.
In the light of NIS2, especially the lawyers in the affected organizations are in the process of making checklists and management orientations so that there is room in the budgets and you have your back free on the day we are not on time and someone asks or demands documentation.
That is why, based on our experience, we ask: Do we really have to go through the same mill every time there is regulation on the way regarding data?
The mill looks something like this:
The proposal appears in the EU. Consultants write blogs and newsletters. The internal employees start mapping and management orientation. The Danish authorities implement in Danish law and / or provide guidelines. There is general confusion about interpretation and practical application. And do the authorities really come out and check? There is a widespread non-compliance with the rules. Responsible employees, journalists and advisers rumble loose and call for action. Finally, some decisions are popping up all around. Compliance starts with great irritation between management and those responsible in the organizations, because everything is forced and outside this year's budget.
We are not going through this mill. It is too great a security risk for most organizations. Therefore, we suggest that the managements out there apply a different approach.
What should you do instead?
You do not have to go to the lawyers. You need to go to the IT security and compliance people first. Then go to the lawyers.
If you start with lawyers, your information and cyber security project is born with coercion and threats in your organization, as lawyers assess business risk too narrowly by typically and naturally only incorporating fines and injunctions in their advice and guidance - the right security is typically forgotten. bit.
It is much better if the project is instead driven by common sense and if it actually has the (financial) support of the management. Because if there is no support - it is our claim based on our experience - it will not succeed in establishing and operating an effective information and cyber security function.
Reject lawyers when they come to you with the list of the latest compliance requirements for information and cyber security.
Also reject the compliance and IT security specialists if they can not also relate the project's activities to the rules that, after all, must ultimately also be complied with (mapping).
With your common sense and your business risk assessment in hand, you can advantageously throw the lawyers in to the security specialists with the message that they can come out when they agree on a prioritization of the activities they want to initiate.
The prioritization must be based on a business risk assessment that prioritises real security, but which, after all, includes the consequence of non-compliance on paper.
We dare to guarantee that the lawyers and the security people will have a hard time in the same room, because the lawyers will not compromise: "Well, the law says so, and I will be fired if we are caught in a violation".
At the same time, the security specialists can and will very rarely formulate themselves in legal terms: "Law is elastic in meters, and it does not provide real security anyway, so lawyers should not interfere at all".
But these are the two fronts that you as management need to take care of using your own common sense in the form of your business risk assessment.
Your plan
You should think the following:
- We must have security, and of course we must protect ourselves against cybercriminals.
- And we must comply with all the old and new legal, directive and regulatory requirements for our particular industry and specific IT activity.
- We must be able to manage, document and report on our efforts.
- But it must be managed by means of a business risk assessment, which neither the lawyers nor the security specialists can prepare in full individually: The lawyers do not understand real security, and the security people do not understand how critical documentation can be in these times in relation to authorities, investors, insurance, etc.
Our contention is that neither the lawyers nor the security specialists can plan an information and cyber security function that can simultaneously document compliance with legal, directive and regulatory requirements. Management can only do this if it has given itself relevant thoughts about risk tolerance and compliance level.
It is time to recognize that the many laws and guidelines place the same basic demands on information and cyber security (see the figure above).
One place is called something one, the other place it is called something else, but the substance is the same.
In certain sets of rules, the requirements are stated in a usable way in the law itself. In other sets of rules, they are stated in the accompanying executive order or guidance. In other cases, we can only see what we really need if we look at case law. But it's not that crucial. The lawyers will probably have to deal with that.
To get back on track: Management needs to define risk tolerance and compliance levels. If management does not do this, employees, security personnel, lawyers and consultants will not be able to perform their duties. And what's worse: Your information and cybersecurity features are not working. And if it is the case that your information and cyber security function does not work, it is a matter for the general meeting, the municipal director, the group management, the head of department and the like.
Once the need for the information and cyber security function has been assessed and planned in the light of risk tolerance, lawyers can be allowed to work:
- They must map out what requirements you are subject to by filling in the following formula: General requirements (NIS2, GDPR) plus sector requirements (Finance, Health, etc.) plus requirements for the IT activity itself (profiling, whistleblowing, face recognition, etc.) minus overlapping requirements (is there double regulation in, for example, GDPR and requirements for IT security in the financial sector?) equal to the final requirements for your information and cyber security function.
- They must then legally qualify the planned information and cyber security function against the final requirements: What is it that we have planned / already do that met one or more requirements on the final requirements list in whole or in part?
- Finally, they must indicate the level of compliance that the implementation of the planned and possibly existing information and cyber security activities will result in.
Management must now either accept the level of compliance for a given period until the issue is raised again as part of the annual cycle, or ask the lawyers to state the specific activities needed to improve the level of compliance.
The lawyers must specify the improvement activities in such a way that they must not come back with an answer before they have clarified the activities with the security people, so that the lawyers' Solution is actually formulated into your planned and possibly existing information and cyber security function.
Thus, when both lawyers and security people have succeeded in formulating an information and cyber security function that stays within the risk tolerance and compliance level accepted in the business risk assessment, management can press start.
And remember now .. And finally: Drop to become 100% compliant. It can not be done. Nor with Joakim von And's money tank. It must thus be included in your business risk assessment that you can not move your organization into the future without the risk of fines or IT breakdowns. But you do not have to say that to either the security people or the lawyers - it must not be a sleeping pad.
